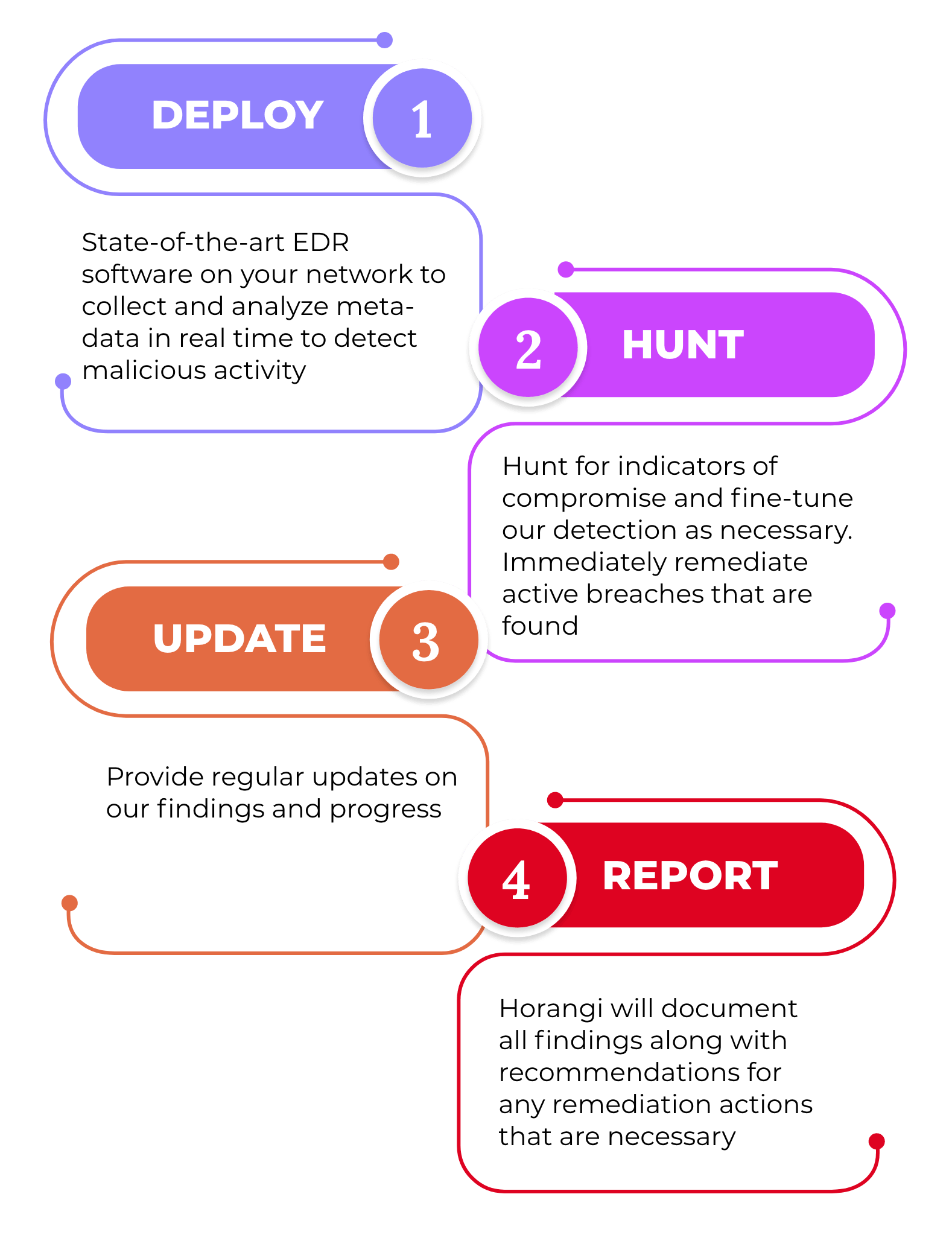
Cyber Security Gap Analysis and Roadmap Development. In this upcoming webinar CEO of LGMS MrFong Choong Fook will reveal the comprehensive view of Compromise AssessmentThe Industry expert is ready to answer your question about Cyber Security.

Compromise Assessment Cybereason Assessments
We are focused on identifying the cyber attacks that these first lines of defence may have missed.

. In an increasingly complex and dynamic threat landscape now more than ever organizations need to understand the. Cybersecurity Posture and Maturity Assessment. In an interview with Information.
It takes organizations an average of 191 days to identify a data breach. Compromise assessment is meant to answer whether the network or systems are compromised. Bank Negara of Malaysias Risk Management in Technology.
Compromise Assessment is an advanced threat diagnostic ATD that detects the clear and present cyber dangers that already exists in your organization. Compromise Assessment wizlynx group Malaysia. Bahasa Malaysia Malay Nederlands.
LGMS Reports are accredited by TÜV Austria to be accepted as part of the certification compliance baselines for various TÜV TRUST IT certification programs. Compromise assessments CA answer the fundamental cyber security question Are we breached. Compromise Assessment Firmus 2020-06-14T1449110800.
1 To comply with local laws regulations Eg. The lab is to provide cybersecurity testing and certifications to organizations worldwide. In assessing the application BNM will take into account amongst others the nature and sufficiency of the financial resources of the applicant as a source of continuing financial support to the licensed person and the business record and experience of the applicant and review whether the application will be in the best interest of Malaysia.
Compromise Assessment ServiceYour essential post-breach strategy for detecting systems already compromised by attacks that are too sophisticated for your existing security controls to catch. 2 To identify the presence of any security breaches. Through identification of footprints left by attackers suspicious indicators in the network as well as abnormal usage computer resource all could lead to the discovery of a potential compromise within your organization.
Usually there are a few reasons companies do a Compromise Assessment. Our CA service delivers a high-level review and audit of your organizations IT environment based on suspicious user behaviors logs compliances policies Indicators of Compromise IOCs or any evidence of malicious activities to identify attackers currently. Compromise Assessment - NETASSIST M SDN BHD Compromise Assessment NetAssist conducts survey of a network and its devices to discover unknown security breaches malware and signs of unauthorized access.
We will seeks to find attackers who are currently in the environment or that have been active in the recent past. OTP or one-time password refers to an alphanumeric or numeric code. The compromised or not state of your environment your ability to identify vulnerabilities your ability to eliminate risks This is essential in running an effective SOC Security Operations Center.
Download Datasheet Demo To establish trust in the IT environment for the board and executives CyberStash conducts forensic-level analysis across the entire IT fleet at a. Our approach to Compromise Assessment The most sophisticated threat actors dedicate their time to finding ways of evading detection from traditional defence mechanisms such as antivirus. Why has Bank Negara Malaysia BNM mandated Large Financial Institutions to perform Compromise Assessment.
Increasingly companies around the world understand that Compromise Assessments are a basic business imperative as they enable them to. Our Compromise Assessments are an essential business need for all organisations. Over the last few years the complexity sophistication and stealth of new cyber security threats have grown rapidly.
While penetration tests focus on finding vulnerabilities a compromise assessment focuses on whether an organization was breached without knowing it he explains. Comply with industry regulations Avoid straining customer relationships as a results of breaches and leakage of sensitive data. Our solution Using Deloittes Cyber Compromise Assessment CCA on your estate will help identify if there is a current or indicators of a past compromise of your network - utilising the latest threat intelligence and detection techniques.
This is confirmed by recent breach. Malaysia through operations of branches and subsidiaries. Vigilant Asia is an award-winning MSSP delivering compromise assessment services in Asia using ThreatDefence XDR platform.
What is Compromise Assessment. They want to know if youre compromised can identify the compromise and if you can come up with an effective incident response strategy. Understanding when we are breached and resolving it should be the top priority.
Material technology projects refers to projects which involve critical systems the delivery of essential services to customers or counterparties or compliance with regulatory requirements. Conventional computer protection technologies have become less effective and are no longer able to guarantee the security of company assets. Secure Software Development Lifecycle.
The approach is designed to be light-touch with simple and temporary monitoring installations. Performing a compromise assessment gives you confidence in your awareness of. Enterprise Security Professional Certification.
TÜV Austria Cybersecurity Lab is established in Malaysia as a joint venture between TÜV Austria and LGMS. He further explained that in Malaysia a compromised assessment is an exercise required by the local central bank to ensure the financial institutions FIs gain visibility to answer three basic questions.
What Is Compromise Assessment The Benefits How It S Different How By Cycraft Technology Corp Cycraft Medium

Compromise Assessment 7 Things You Should Know Lgms Blog

Compromise Assessment Malaysia Uncover Hidden Security Risks Firmus

Compromise Assessment 7 Things You Should Know Lgms Blog
Compromise Assessment Service Cyberstash

Compromise Assessment 7 Things You Should Know Lgms Blog
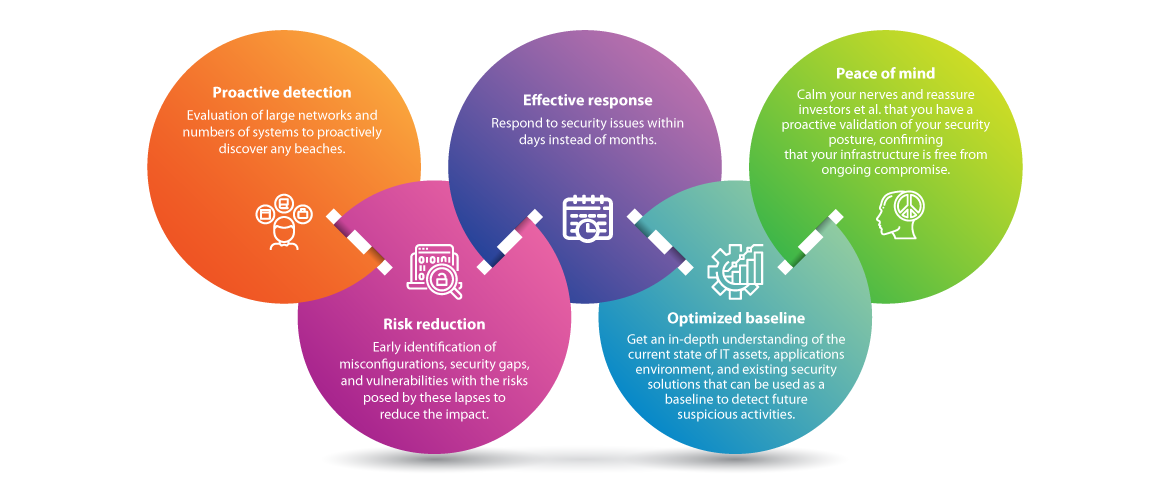
Key Benefits Of Compromise Assessment Infographic Ec Council Global Services Egs

Compromise Assessment Condition Zebra Cyber Security Company Malaysia
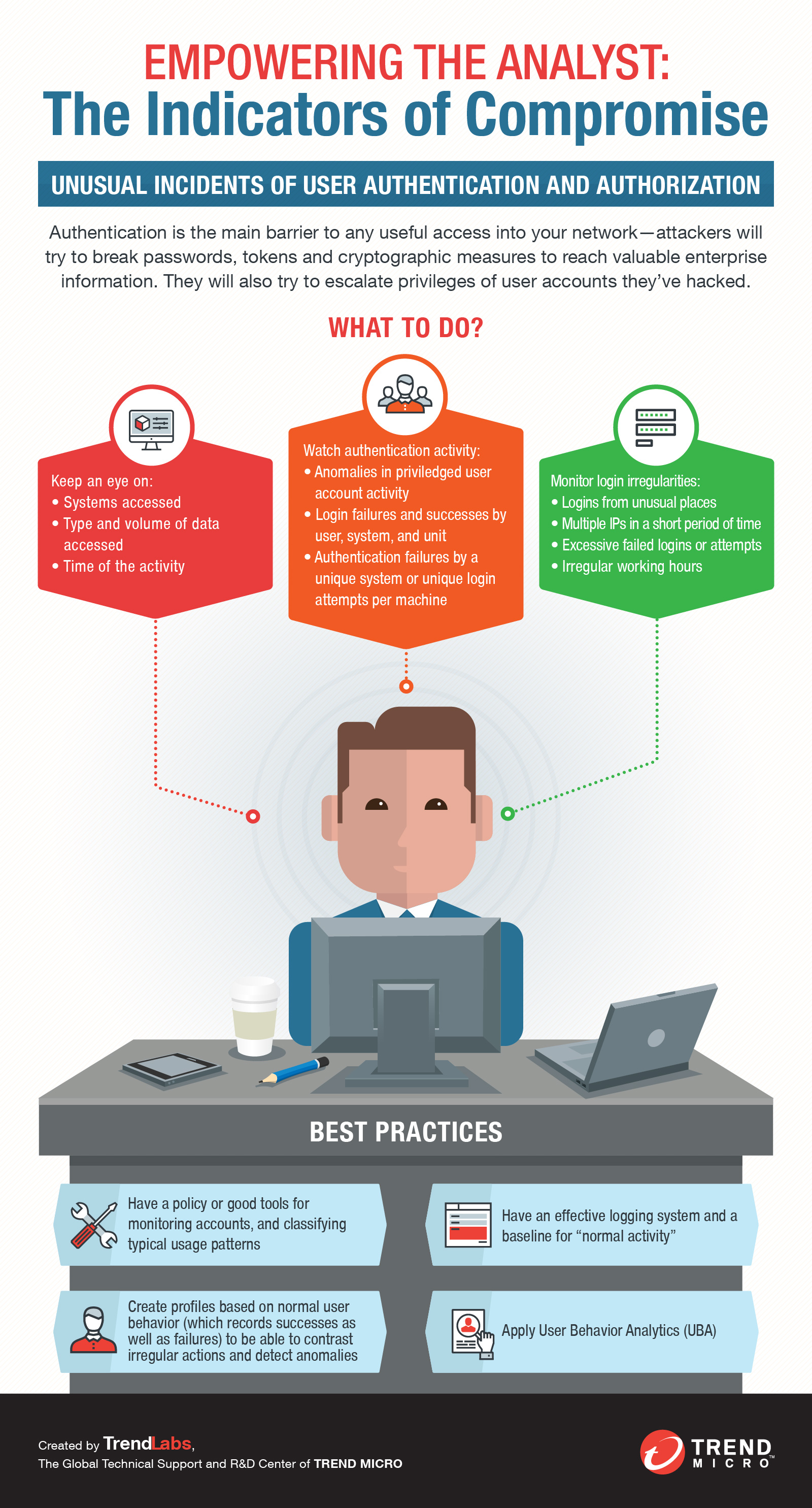
Indicators Of Compromise Definition

Indicators Of Compromise Definition

Compromise Assessment 7 Things You Should Know Lgms Blog
What Is Compromise Assessment The Benefits How It S Different How By Cycraft Technology Corp Cycraft Medium

Cyber Compromise Assessment Deloitte China Risk Advisory

Compromise Assessment Ec Council Global Services Egs

The World Cup Is Here And With It Comes Excitement Pride Competition And Sportsm Physical Education Lessons Education Lesson Plans Physical Education Games